Management¶
Administrators¶
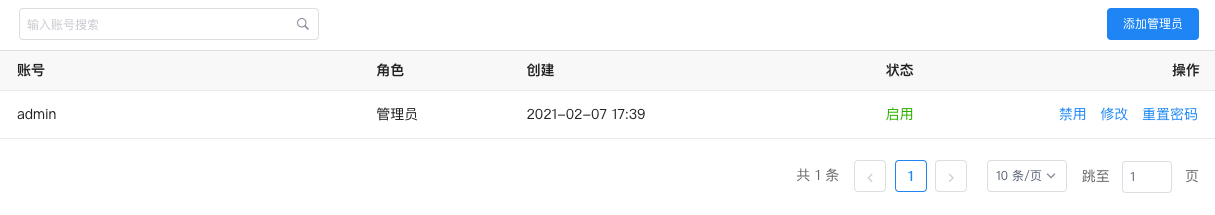
On the Settings > Administrators page, you can search, add, modify, and disable/enable all administrator accounts.
Currently, there are two types of administrator account roles: Administrators and Developers:
- Administrator: Has all management permissions and can log in to the management backend and the DataFlux f(x) development platform;
- Developer: Can only log in to the DataFlux f(x) development platform.
Add an Administrator¶
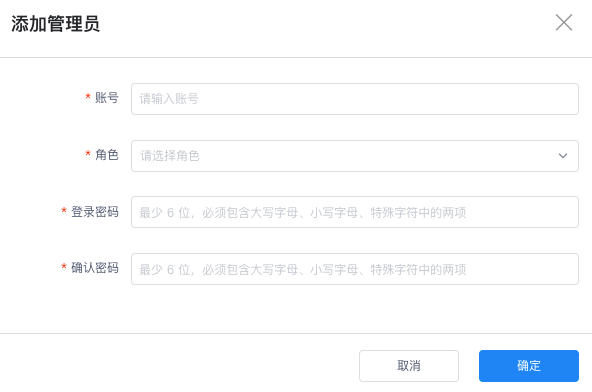
On the Settings > Administrators page, click the Add Administrator button in the top-right corner. In the pop-up dialog box, fill in the administrator account information, select role permissions, input the password, and click confirm to add a new administrator.
Modify¶
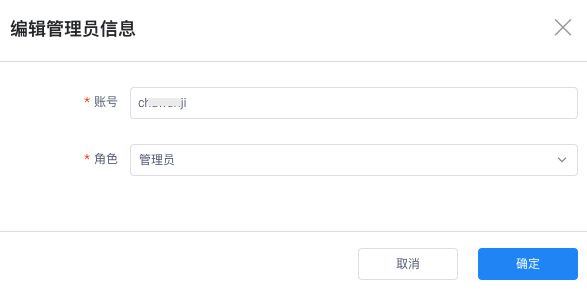
On the Settings > Administrators page, click Modify to the right of the account to enter the Edit Administrator Information page. You can modify the administrator account and role permissions here.
Reset Password¶
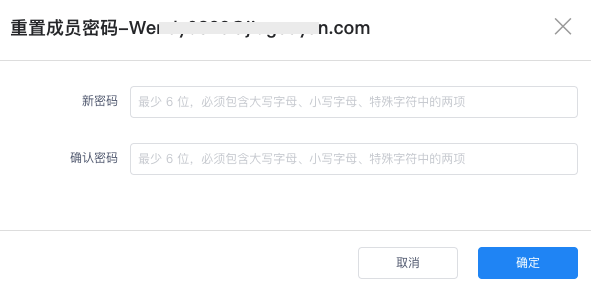
On the Settings > Administrators page, click Reset Password to change the password for that administrator account.
Disable/Enable Members¶
On the Settings > Administrators page, click Disable or Enable to the right of the account to toggle the account status.
Note: If the currently logged-in account is disabled, the login account information will become invalid, and you will automatically be logged out of the management backend. Before re-enabling, you will not be able to log back into the management backend.
Basic Information¶
On the Guance management backend Settings > Basic Information page, you can customize settings such as the default language, product name, logo, and browser display icons.
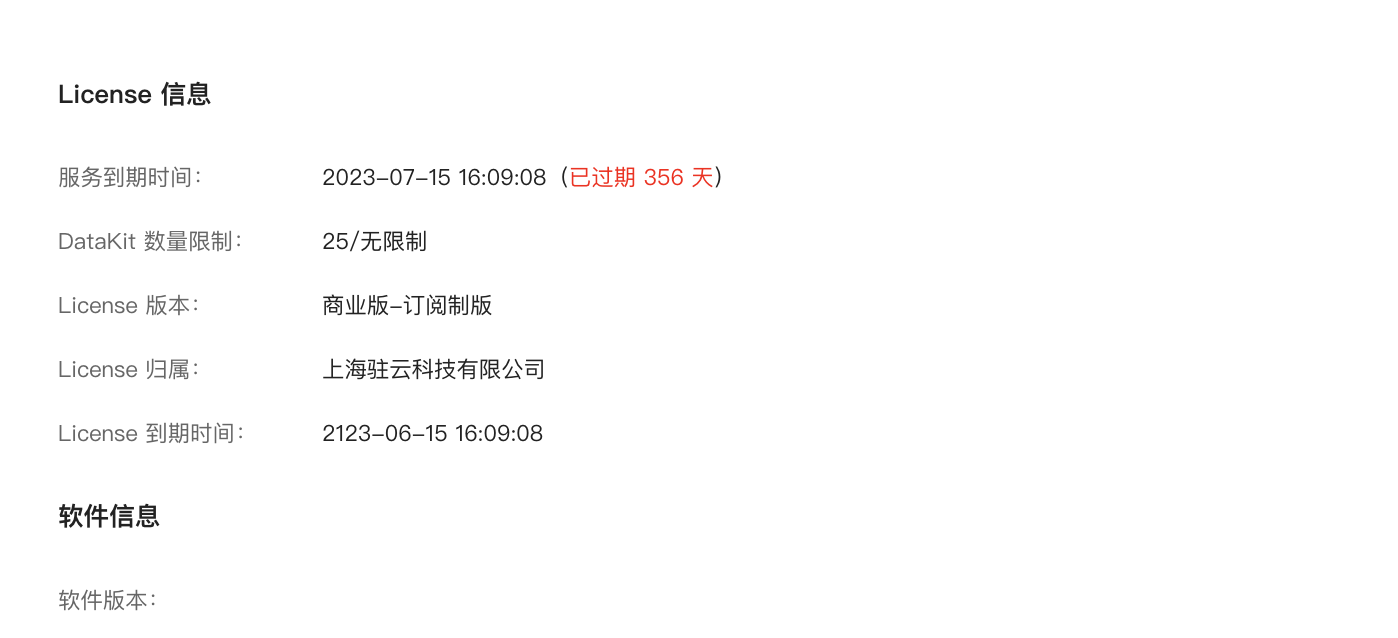
Additionally, you can view workspace License information and software information, including service expiration dates, DataKit quantity limits, License versions, ownership, and expiration times:
User Settings¶
On the Settings > User Settings page, you can modify the password for the currently logged-in account.
Mapping Rules¶
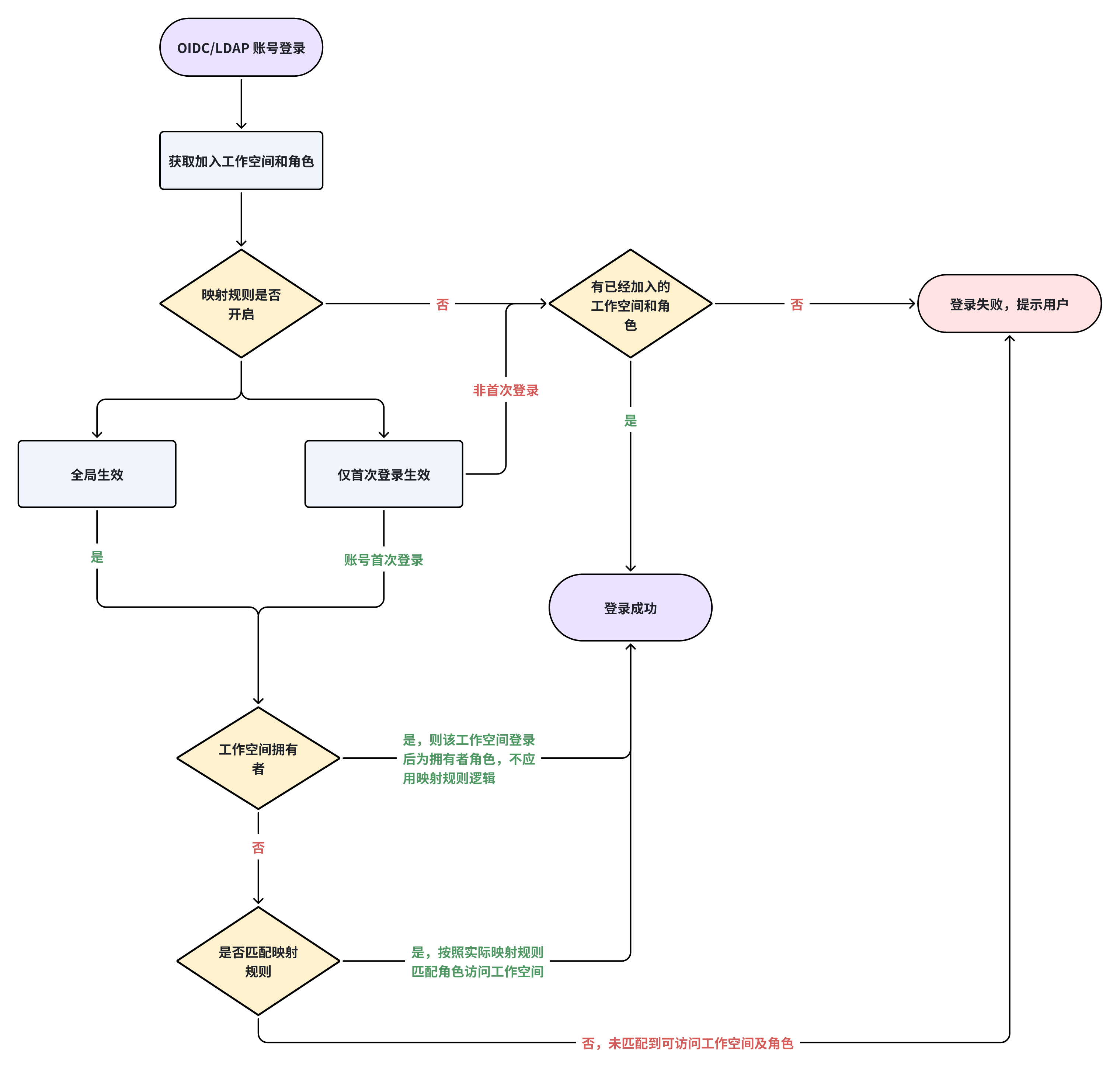
The Guance Deployment Plan supports single sign-on using OpenID Connect/OAuth 2.0/LDAP protocols and allows configuration of mapping rules for these SSO accounts. After enabling mappings, enterprise employees can be dynamically assigned access permissions based on their allocated roles, allowing them to access Guance accordingly.
When a single sign-on account is set as the workspace owner, note the following:
The account's role in this workspace is fixed as the owner and is not affected by mapping rule matches. Conversely, the actual mapping rules determine the role for accessing the workspace.
Besides configuring mapping rules in the management backend, you also need to configure Keycloak single sign-on mapping rules. Both configurations must be completed for the mapping rules to take effect.
Application Scope¶
In Management > Mapping Rules, you can choose between Only Effective on First Login and Globally Effective for the scope of application of the mapping rules:
Only Effective on First Login
When you enable this option, if a user logs in via SSO for the first time, they will be dynamically assigned to a workspace and given a role according to the mapping rules.
Note: Accounts that have already logged in via SSO will not be affected by the mapping rules.
Additional Effectiveness
After enabling, SSO accounts will be assigned workspaces and roles according to the mapping rules, keeping their existing workspaces and roles unchanged.
For example, if a member originally has the Standard role and a new mapping rule assigns the Administrator role, they will simultaneously possess both the Standard and Administrator roles.
Globally Effective
When you enable this option, the current roles in the workspaces of users logging in via SSO will be revoked, and roles will be dynamically assigned according to the mapping rules matched with the attributes provided by the identity provider. If no matching mapping rules are found, the user account will be stripped of all roles and will not be allowed to log in to Guance workspaces.
Note: Every login requires going through the dynamic workspace joining and role assignment process; once the corresponding mapping rules are deleted from the management backend, the user's associated workspace will be considered inaccessible.
Not Enabled: Users logging in via SSO will continue to hold the roles previously assigned to their accounts, unaffected by changes in assertions from the identity provider side.
Add Mapping¶
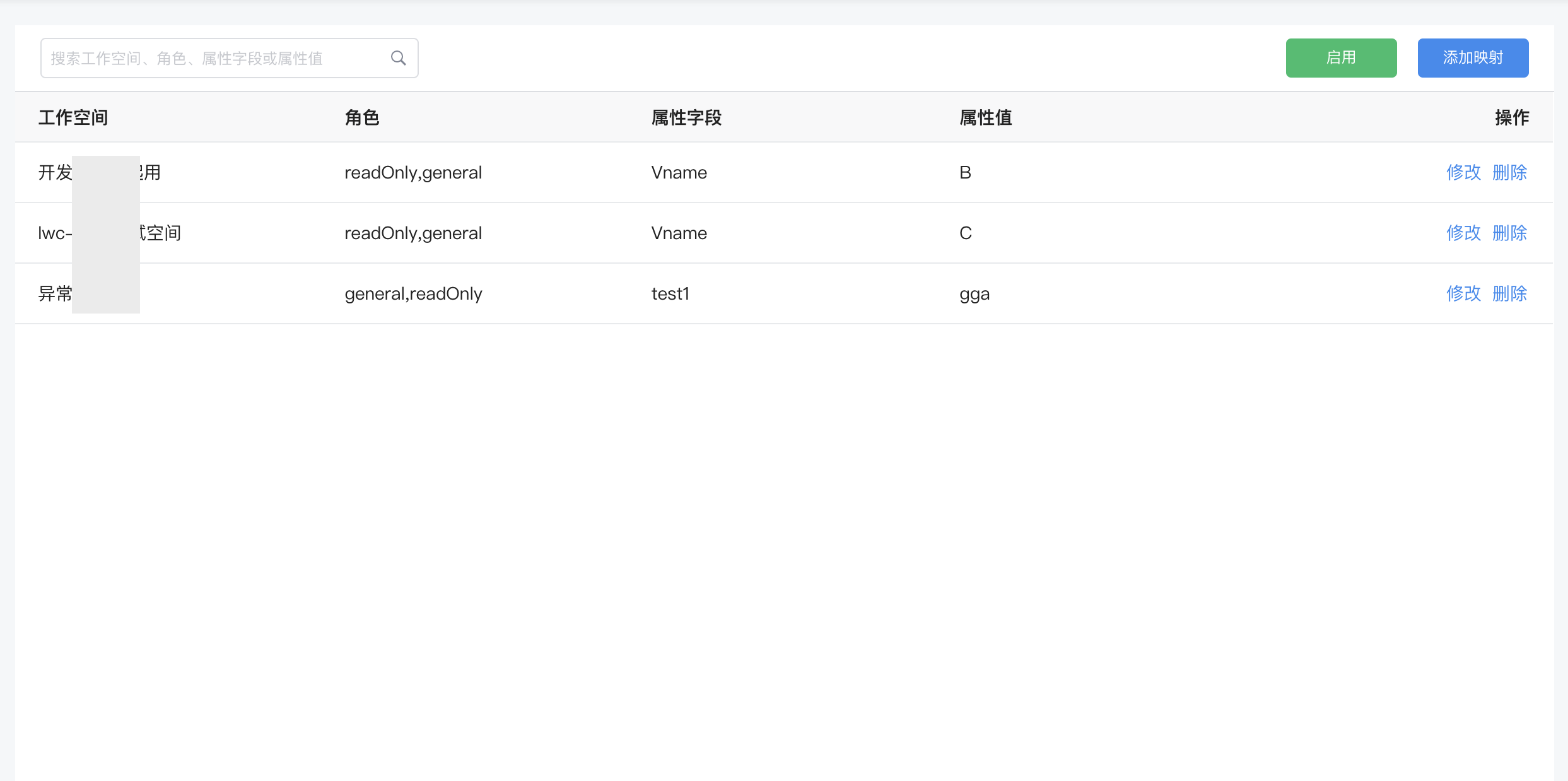
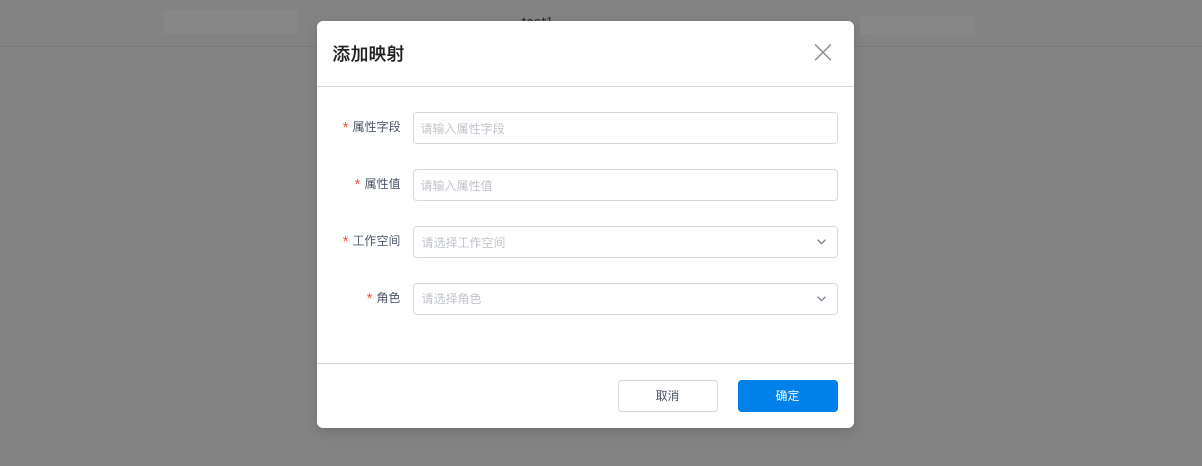
After configuring the mapping rules, the management backend will add members to the corresponding workspaces and assign them the corresponding roles based on the mapping relationships. On the Management > Mapping Rules page, click Add Mapping.
In the dialog box for creating a new mapping, input the required attribute field and its attribute value, select the role, and click Save.
| Field | Description |
|---|---|
| Attribute Field/Attribute Value | The attribute fields and values configured in the mapping must match those set on the IdP account for successful validation. After successful validation, when the IdP account logs in, the account will be granted the role permissions specified in the mapping. |
| Workspace | All workspaces in the management backend. |
| Role | Guance supports four default member roles: Owner, Administrator, Standard, and Read-only. You can also create new roles in Role Management and assign permission scopes to meet different user needs. |
Search/Edit/Delete Mapped Roles¶
- Search: Supports filtering mapped roles by workspace, role, attribute field, and attribute value;
- Edit/Delete: Supports clicking the Edit/Delete button to the right to modify the already configured mapped roles. Modifications do not affect the roles and permissions of currently logged-in accounts but will impact subsequent user logins.
Operation Audit¶
Go to Management > Operation Audit to view all audit events.
Time Widget¶
By default, all audit events are listed automatically, and you can add a time range for further filtering.
After selecting a date range, events within the selected time range will be listed. The default start time is 00:00:00, and the default end time is 23:59:59.
- After selecting a time range, click Select Time to customize the time range;
- Click Clear to remove the time filter condition.
Search & Export¶
| Action | Description |
|---|---|
| Search | You can search audit event titles and descriptions. |
| Export | Clicking the button exports the current audit events as a CSV file. |
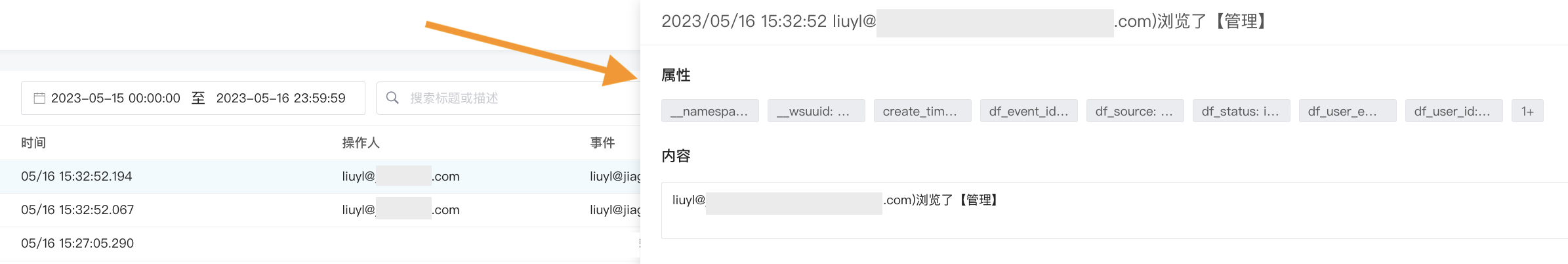
Audit Event Details Page¶
Click on a specific event in the list to expand its details page. Within the details page, you can view the properties and content of the audit event.
Workspace Audit Events¶
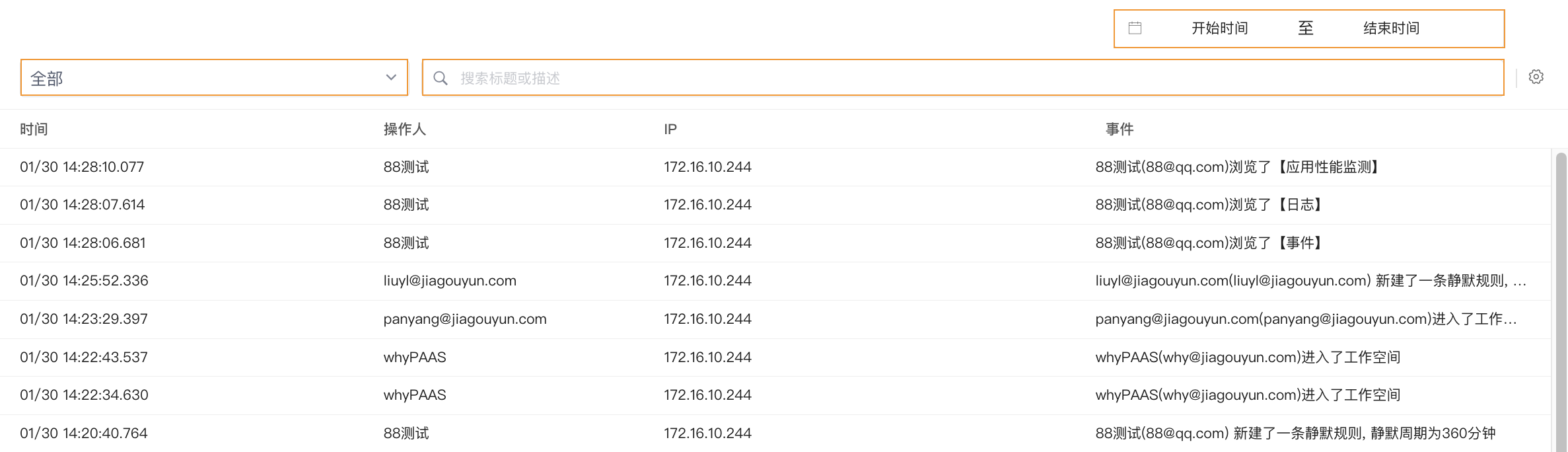
You can view audit events for all workspaces.
You can filter events based on workspace or time range, or directly input relevant titles and descriptions for search and positioning:
Security Settings¶
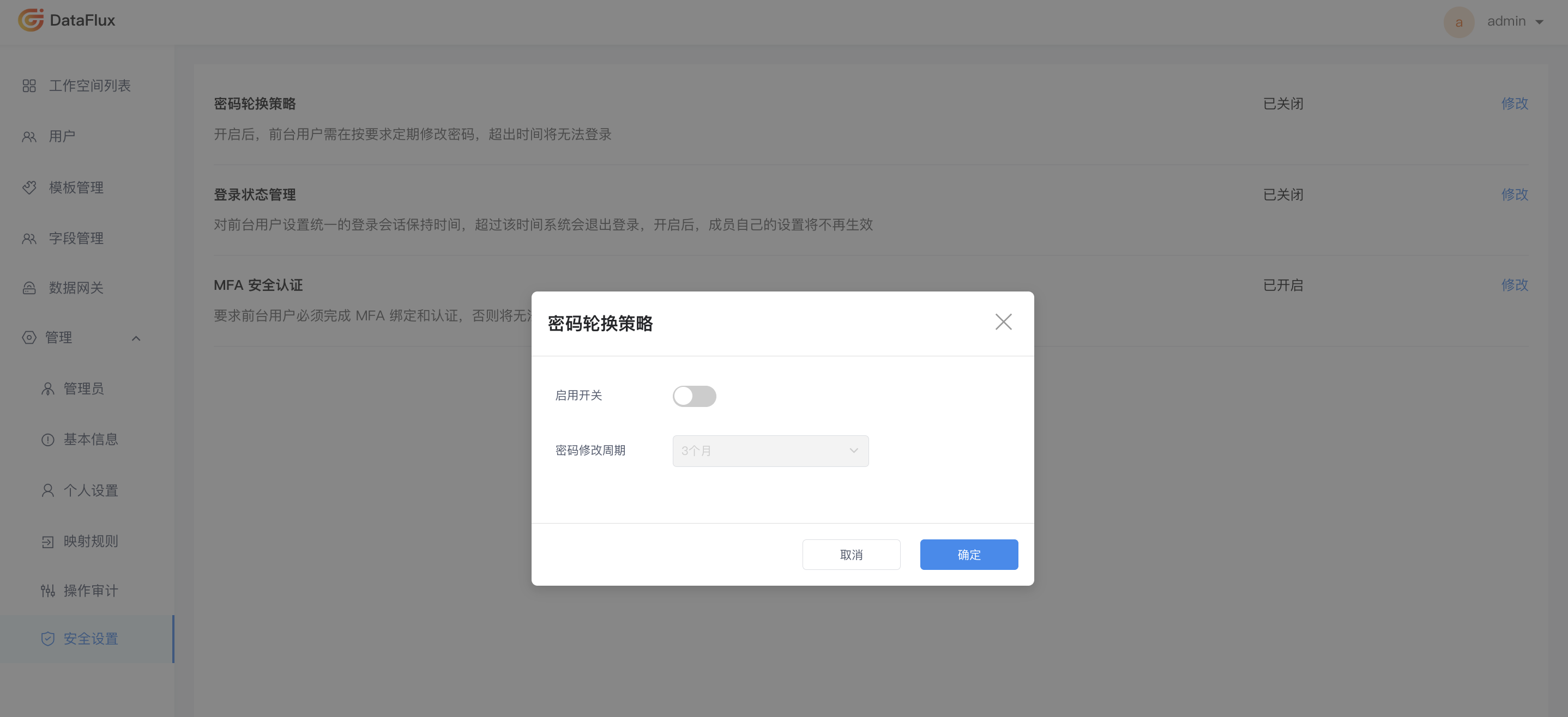
Password Rotation Policy¶
To further enhance the security of the management backend, the Guance Deployment Plan provides a password rotation policy. By default, the password rotation policy is not enabled.
You can choose a password validity period as needed: 3 months, 6 months, or 12 months; it is turned off by default.
Note: Starting 7 days before the password expires, you will receive daily reminder emails about the impending expiration of your management backend password. You can reset your password via the email, and the new password cannot be the same as the current one.
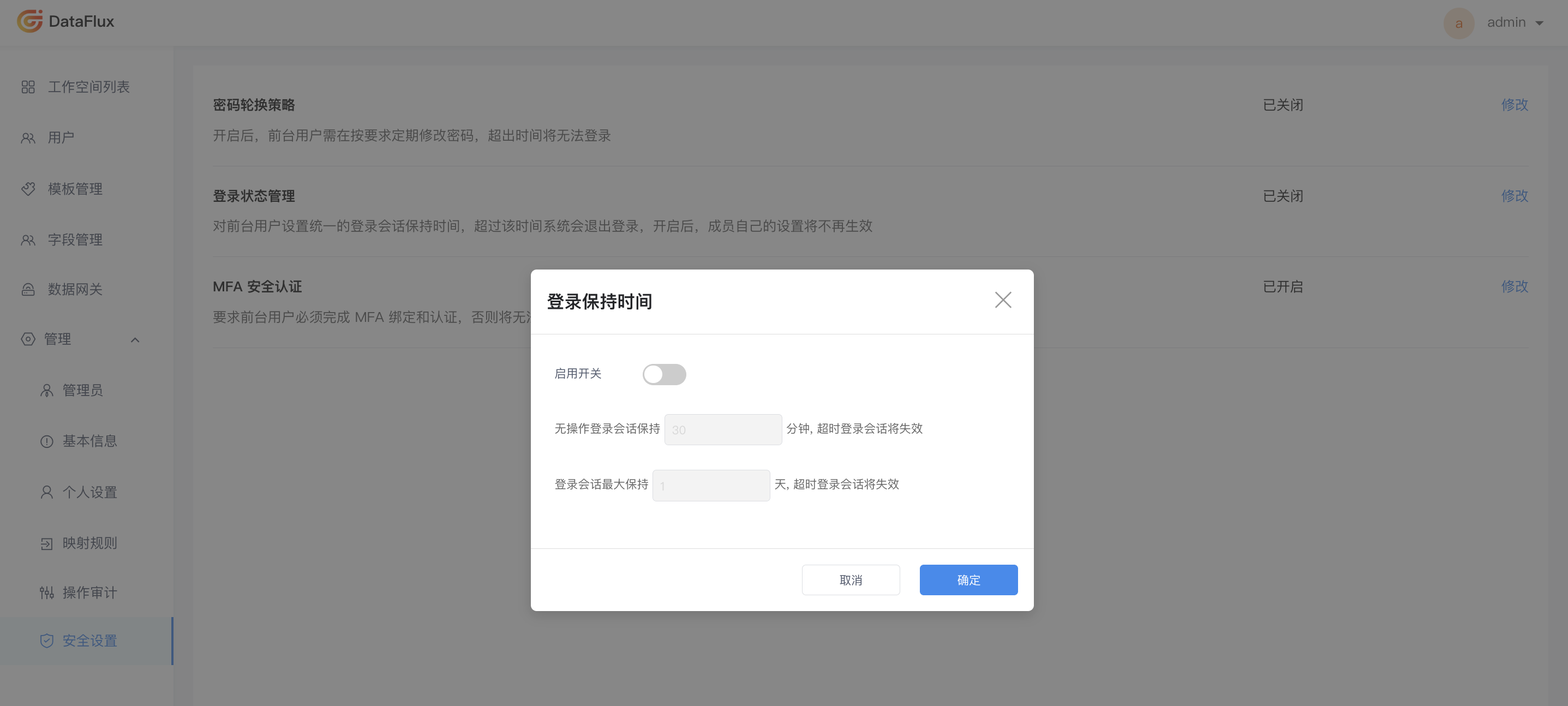
Login Session Management¶
Guance supports unified session duration settings for frontend users. When turned off, members in the frontend workspace can freely configure session durations; when turned on, members cannot make free modifications and will uniformly follow the settings here.
In the Session Duration, click Modify to adjust the default session durations, including idle session duration and maximum session duration. After setting, expired sessions will become invalid.
- Idle session duration: Supported range is 30 to 1440 minutes, default is 180 minutes;
- Maximum session duration: Supported range is 1 to 7 days, default is 7 days.
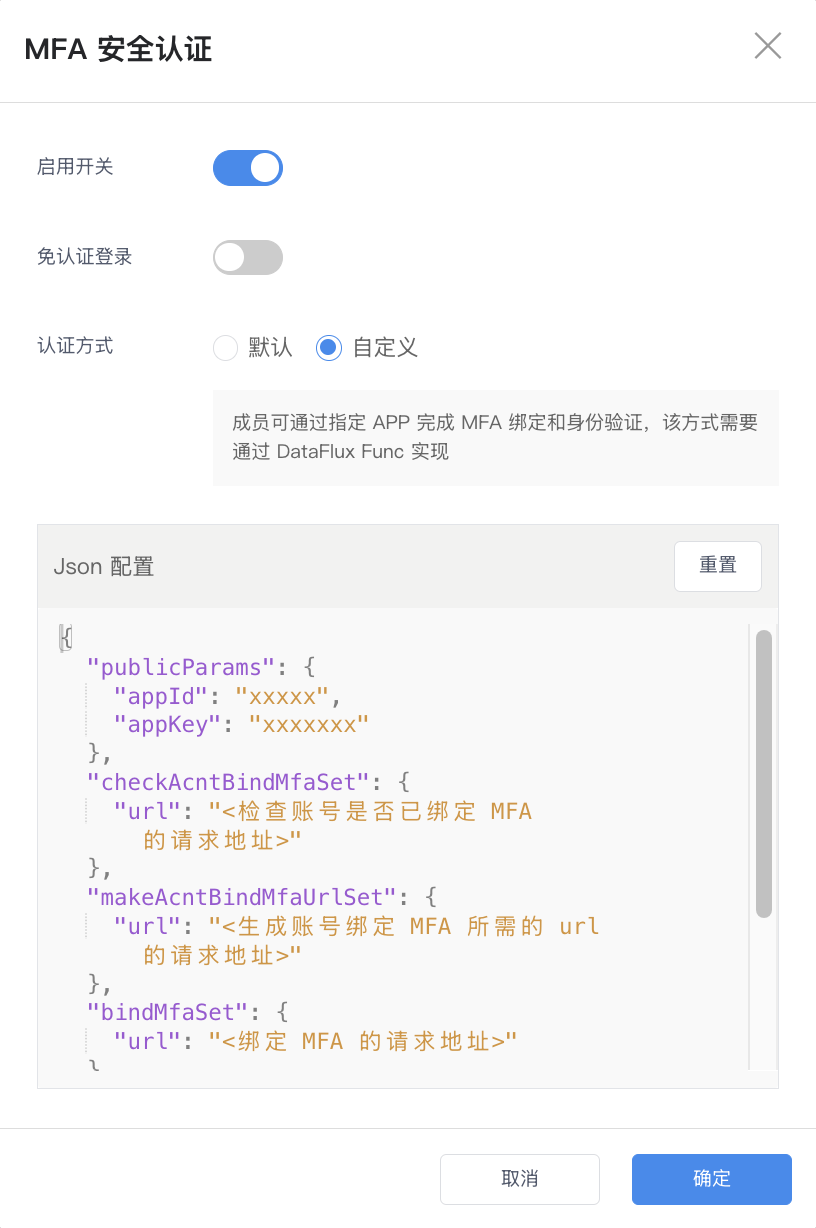
Console/Management Backend MFA Security Authentication¶
Both Guance workspaces and the management backend provide mandatory multi-factor authentication (MFA) management to add an extra layer of security beyond account usernames and passwords. After enabling MFA authentication, you will need a second verification during login to increase account security.
If you do not need secondary verification, you can check "Login without authentication" to simplify your login process.
- Default: Members can use any authenticator app to complete MFA binding and authentication;
- Custom: Members must use a specified app to complete MFA binding and authentication, which requires implementation via DataFlux Func. In custom MFA mode, when users unbind MFA, the MFA on the Guance side for that account will also be unbound.
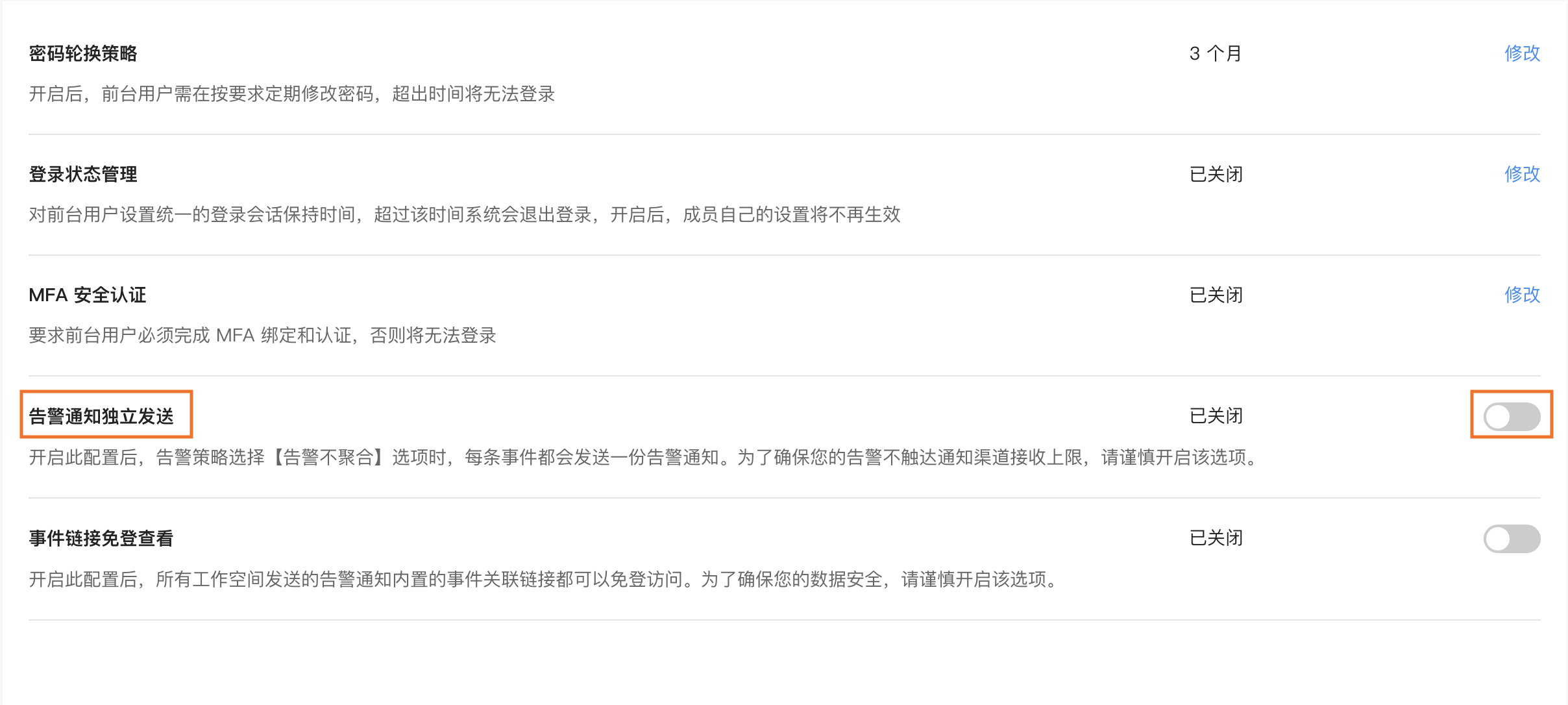
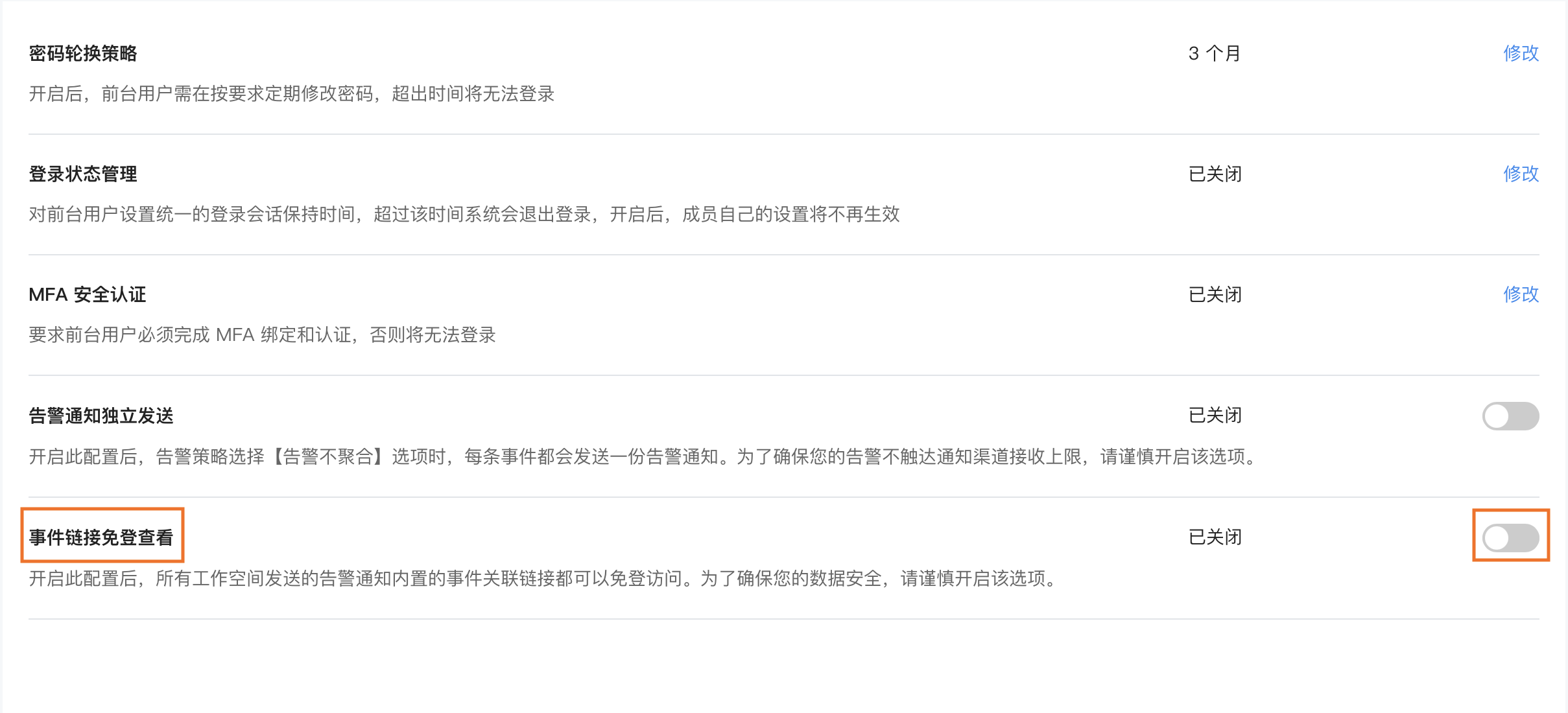
Independent Alarm Notification Sending¶
Guance supports sending alarm notifications independently when monitors detect results under non-aggregated alarm modes.
Under non-aggregated alarm notification mode, alarm events will be merged every 20 seconds and sent to the corresponding notification targets. You can enable/disable independent alarm notifications and configure whether alarm notifications should be aggregated into a single message.
Event Link Public Viewing¶
Supports viewing embedded jump links in alarm notifications via public sharing. You can configure Event Link Public Viewing. After enabling this setting, all event links embedded in alarm notifications sent by workspaces can be accessed without login. Once disabled, all historical public links' viewing permissions will become invalid.
Login Method Management¶
Currently, you can log into the Guance console via local accounts, LDAP accounts, or OIDC, three login methods. Click Modify to manage user account login channels.
- Local account: An account created through Registering Guance;
- LDAP Account;
-
OIDC: Single sign-on via OpenID Connect protocol, refer to:
DataKit Management¶
On this page, managers can view host information for Datakits installed on the current platform, including running IDs, IP addresses, operating systems, hardware platforms, counts, and DataKit versions across different workspaces.
Note: If DataKit runs in gateway mode, the count does not follow physical counts but instead follows CPU Core counts.
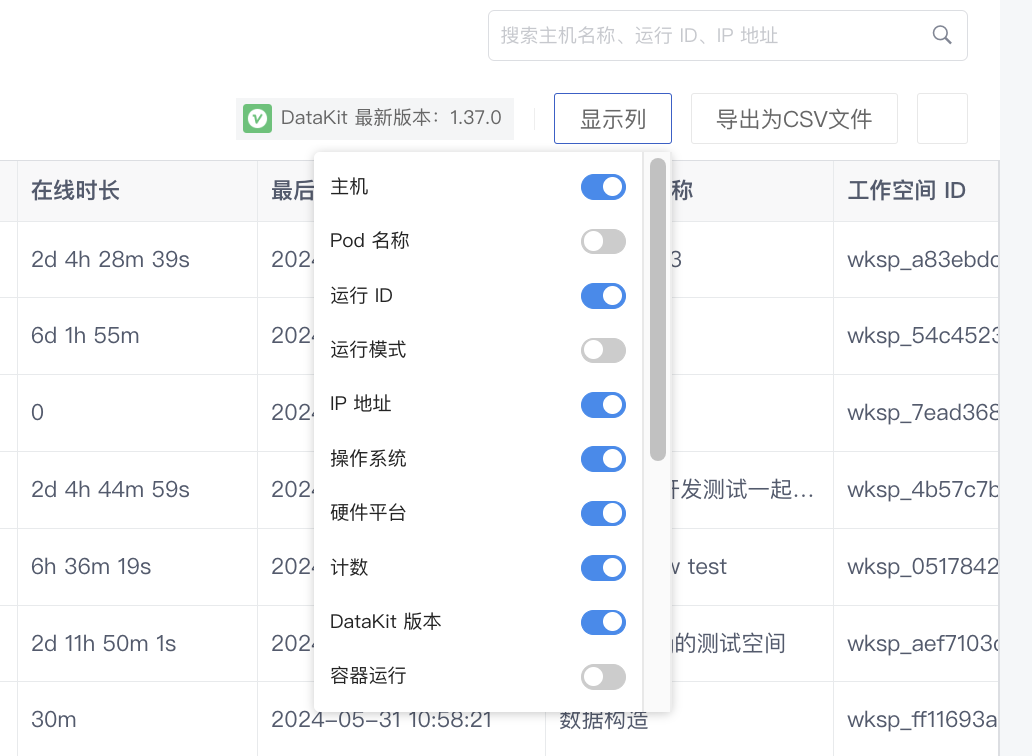
For this list, you can perform the following management operations:
- Click on the workspace or DataKit version dropdown to filter;
- Input host names, running IDs, or IP addresses in the search bar to locate data;
- Select "Show online hosts only" and filter hosts that reported data in the last 10 minutes, 15 minutes, 30 minutes, 1 hour, or 3 hours;
-
Export DataKit inventory data for later problem tracing and capacity expansion reporting;
-
Adjust the displayed columns in the table for customization:
Note: If the number of DataKits used on the current platform exceeds the license limit, you need to monitor the usage of DataKits across workspaces. Additionally, if this situation occurs, management backends and workspace login users will need to proceed with renewal payments, and Guance upgrades will temporarily be unavailable. To increase DataKit usage, contact your account manager to purchase additional quantities.
Global Configuration¶
Incident Level Management¶
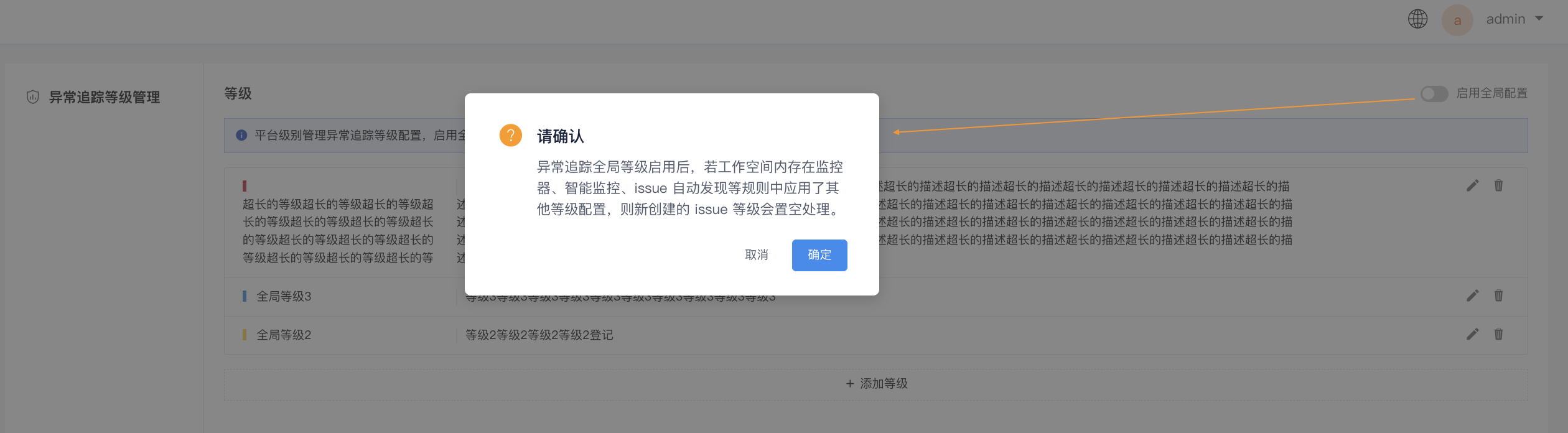
You can manage global issue level configurations for all workspaces from this entry point.
Note: After enabling global configurations, workspace-level incident tracking level settings will no longer apply.
Click Add Level, select the level color block, input the level name and description, and the creation will be successful.
For levels, you can perform the following operations:
- Edit: Click the edit button to modify the current custom level's color, name, and description.
- Delete: Click to delete the current level. After deletion, if the workspace contains monitors, intelligent monitoring, or issue auto-discovery rules applying this level, newly created issues will have their level set to blank.
Global DCA Configuration¶
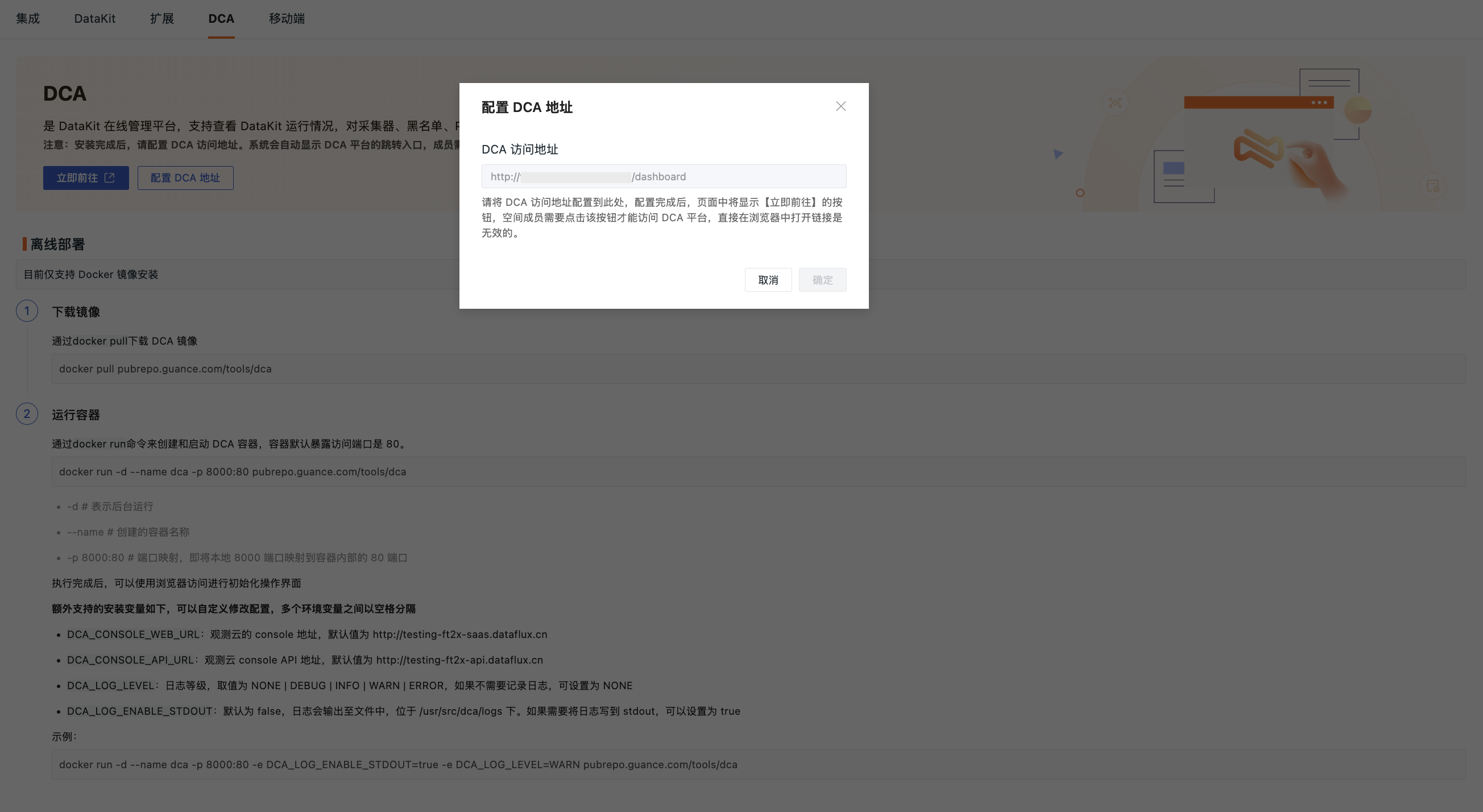
DCA is the DataKit Online Management Platform. On this platform, you can view the DataKit operation status and centrally manage and configure collectors, blacklists, and Pipelines.
After enabling this configuration, the DCA address configuration here will be synchronized to all workspaces, overriding the original DCA address configured in the workspace.
- Enable the switch;
- Input the new DCA access address;
- Click confirm.
After enabling the new configuration here, clicking the "Configure DCA Address" button in the workspace will populate the address with the one configured in the management backend, making it non-editable.
If you choose to disable the DCA configuration, the workspace will revert to its original DCA configuration, at which point you can edit the DCA address.