SSO Management¶
Guance supports SAML-based and OIDC/Oauth2.0 protocol SSO management. Enterprises can manage employee information in the local IdP (identity provider) without synchronizing users between Guance and the enterprise IdP, allowing employees to log in and access Guance through specified roles.
In SSO Management, you can:
- Configure single sign-on based on the corporate domain
- Enable role mapping based on the corporate domain for more precise single sign-on
User SSO¶
If an employee's email matches the domain suffix of the unified identity authentication of the company, they can log in to Guance via this email and access the system according to the configured permissions.
- Navigate to Management > Member Management > SSO Management > User SSO;
- Select SAML or OIDC as needed;
- Start configuration.
Note
- You can create multiple SSO IDP configurations, with a maximum of 10 configurations per workspace;
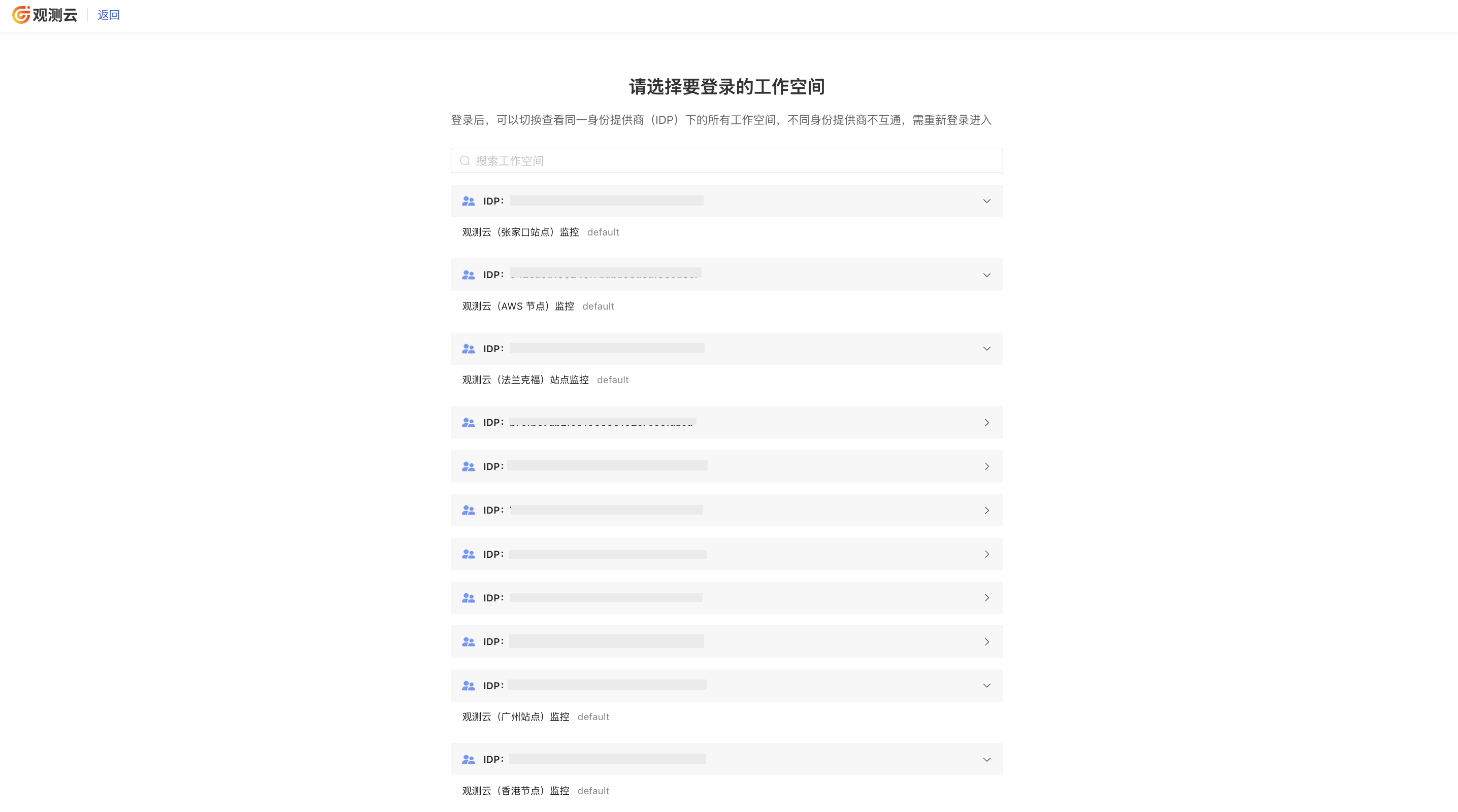
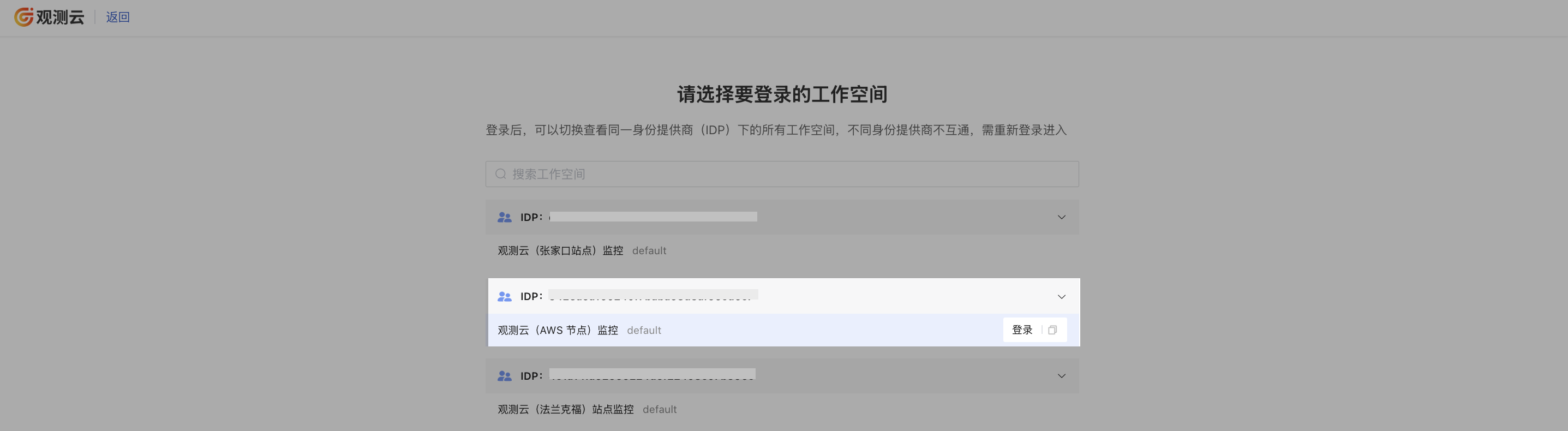
- When configuring the same identity provider SSO single sign-on across multiple workspaces, users who log in via SSO can switch between different workspaces by clicking the workspace option in the top-left corner.
Access Types¶
SSO List¶
Role Mapping¶
-
Enable role mapping:
- SSO login users are dynamically assigned roles based on matching role mapping rules from the
attribute fieldsandattribute valuesprovided by the identity provider; - Users who do not match any mapping rule will have all roles removed and will be unable to log in and access the workspace.
- SSO login users are dynamically assigned roles based on matching role mapping rules from the
-
Disable role mapping: Single sign-on users retain previously assigned roles and are unaffected by changes in assertions from the identity provider side.
Enable/Update/Delete/Import/Export¶
After adding an identity provider, you can enable or disable the current SSO configuration as needed. After enabling, the following operations are supported:
- Update SSO Configuration: This operation may affect the login experience of existing SSO members, so proceed with caution;
- Delete SSO Configuration: This operation will remove the current single sign-on configuration, preventing related members from logging in via this configuration. Proceed with caution;
- Import/Export Identity Providers: Support importing and exporting identity provider configurations, making it convenient to quickly replicate them across multiple workspaces.
Note
- When exporting files, the file name cannot be the same as any existing identity provider in the current workspace.
- Exported files must comply with JSON format standards.
View SSO Members¶
- Member Count: Displays the total number of members who have logged in via SSO.
- Member List: Click on the member count to view the specific list of authorized SSO members.
Email Notifications¶
When enabling, configuring, or deleting SSO, Owners and Administrators of the workspace will receive relevant email notifications.
Login Verification¶
- Log in via email to Guance SSO page: https://auth.guance.com/login/sso;
- Enter the email address configured during SSO creation to access all authorized workspaces for that identity provider;
- Login address;
- Input username, password, etc.;
- Successful login.
Note
- If the workspace has enabled role mapping, but the current user does not match any role or the role mapping is disabled, a prompt of "No access permission" will appear;
- After deleting the identity provider from the workspace, users selecting SSO login will no longer see unauthorized workspaces.