Authorize AWS Using External ID¶
-
Click to proceed with authorization, enter the console.
-
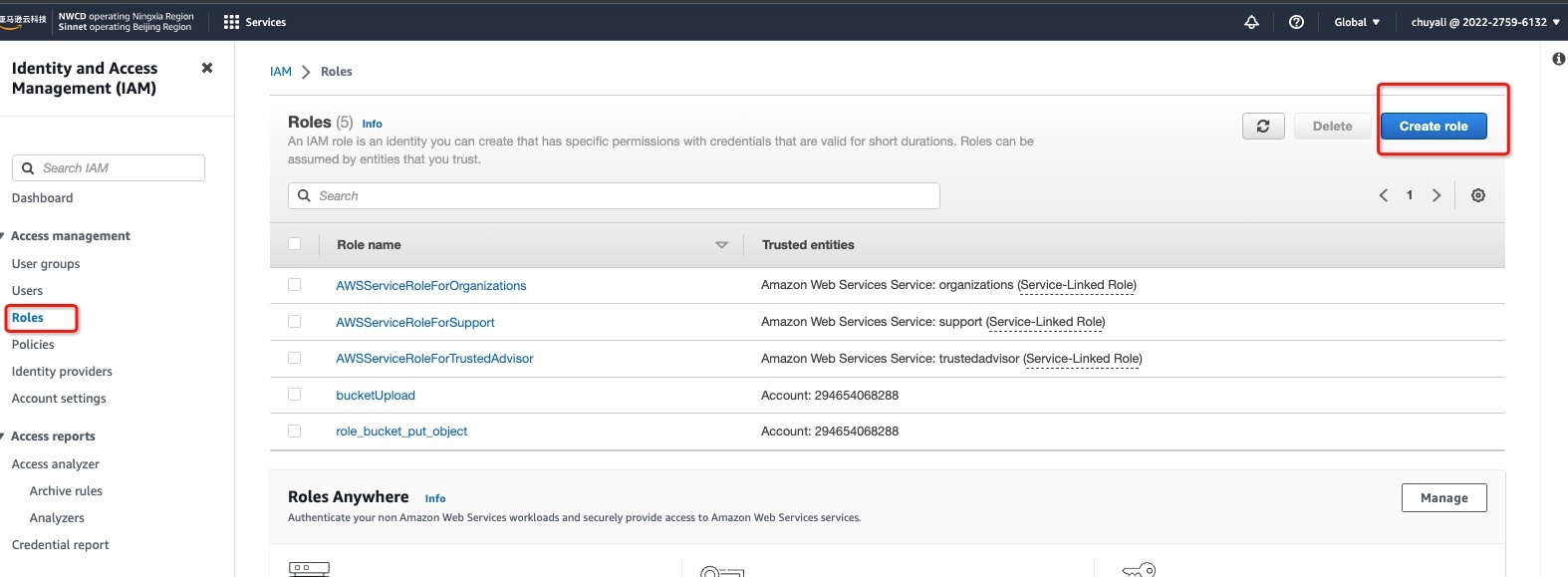
Select IAM
2.1 In the left sidebar, select Roles, and click Create role:
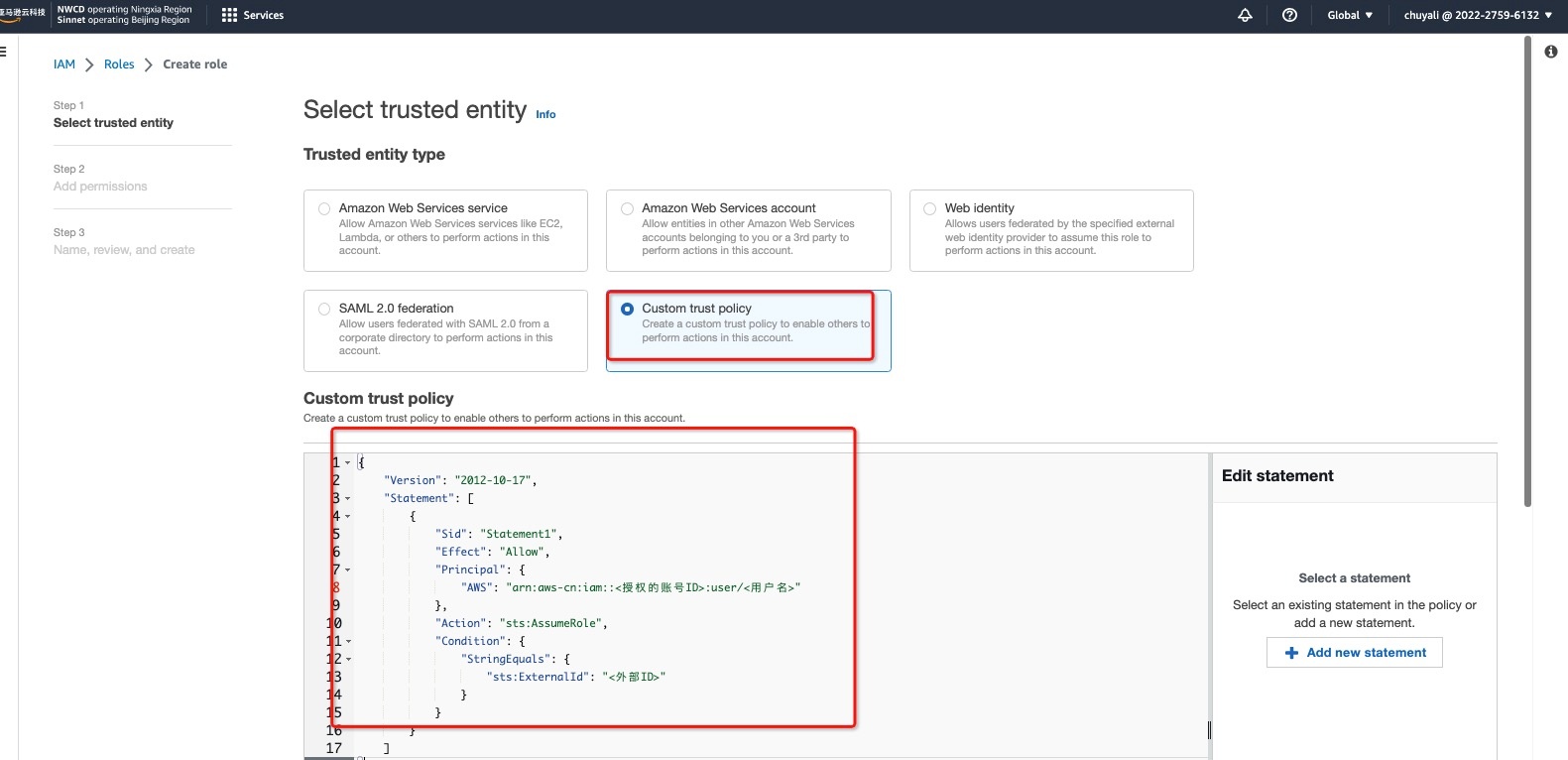
2.2 In Step 1 > Select trusted entity, choose Custom trust policy:
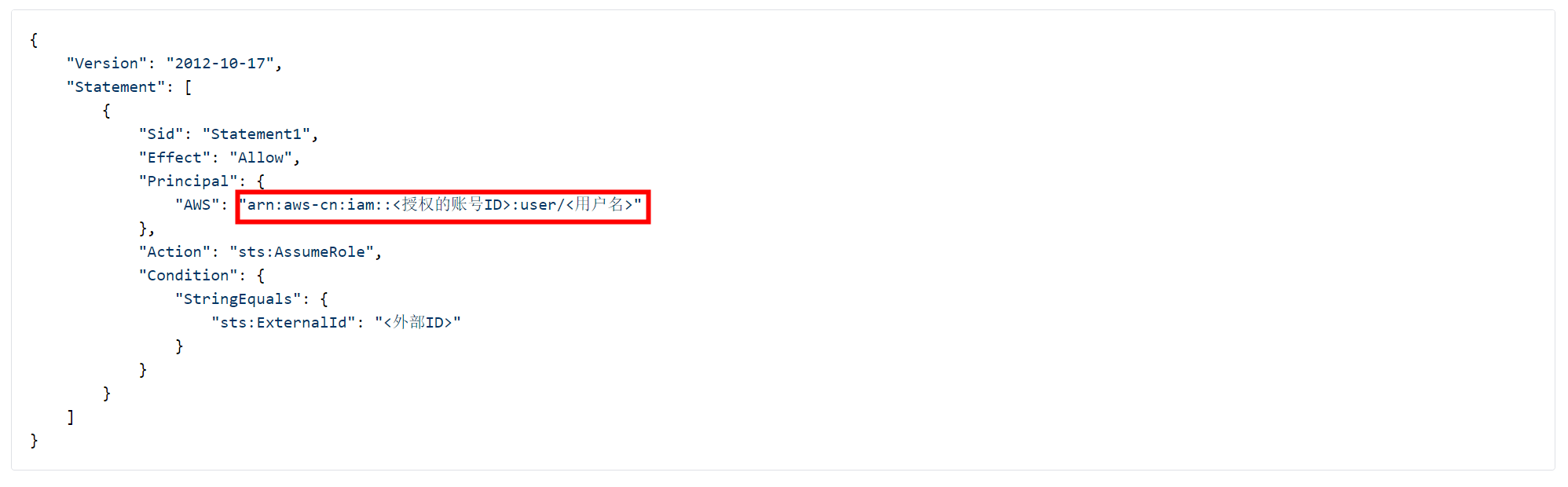
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws-cn:iam::<Authorized Account ID>:user/<Username>"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "<External ID>"
}
}
}
]
}
Warning
When configuring the custom trust policy, you need to fill in Guance's AWS ID and username information.
The actual information to be filled in (this is a fixed configuration): arn:aws-cn:iam::588271335135:user/guance-s3-bakcuplog
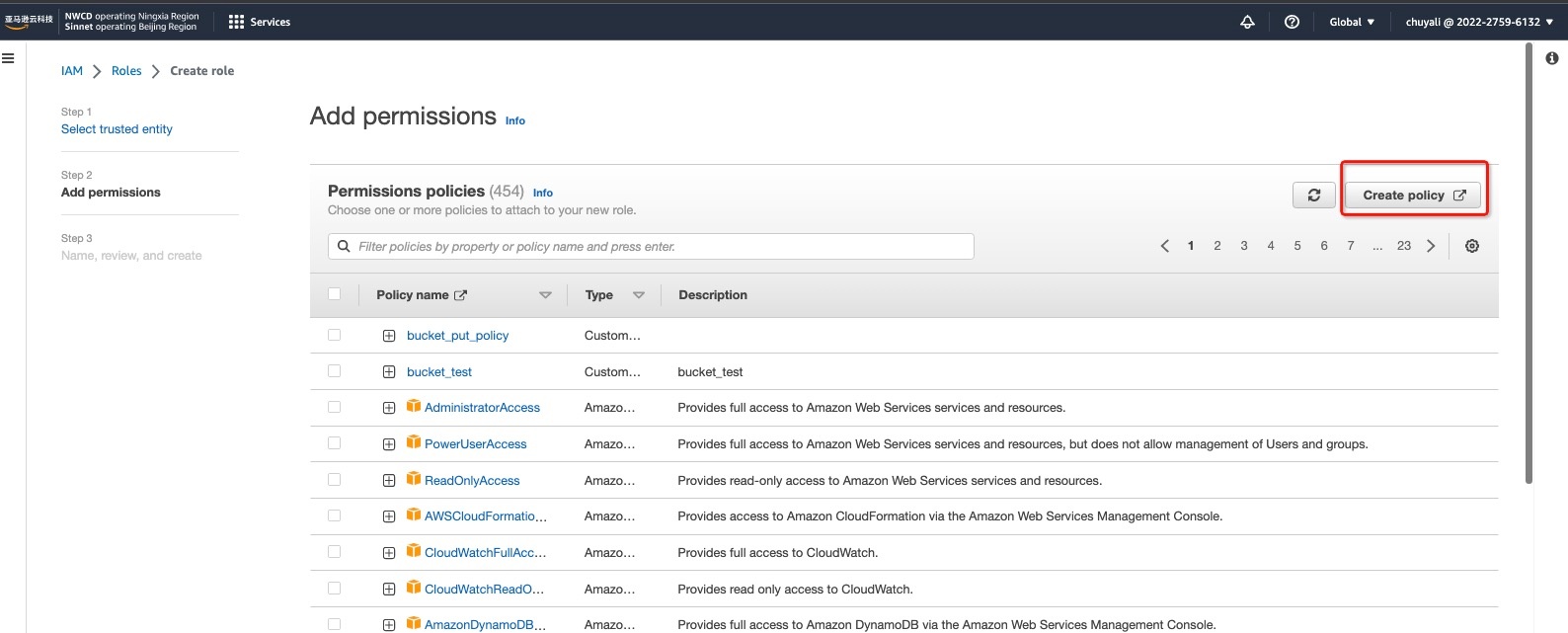
2.3 Click Next, in Step 2 > Add permissions, click Create policy:
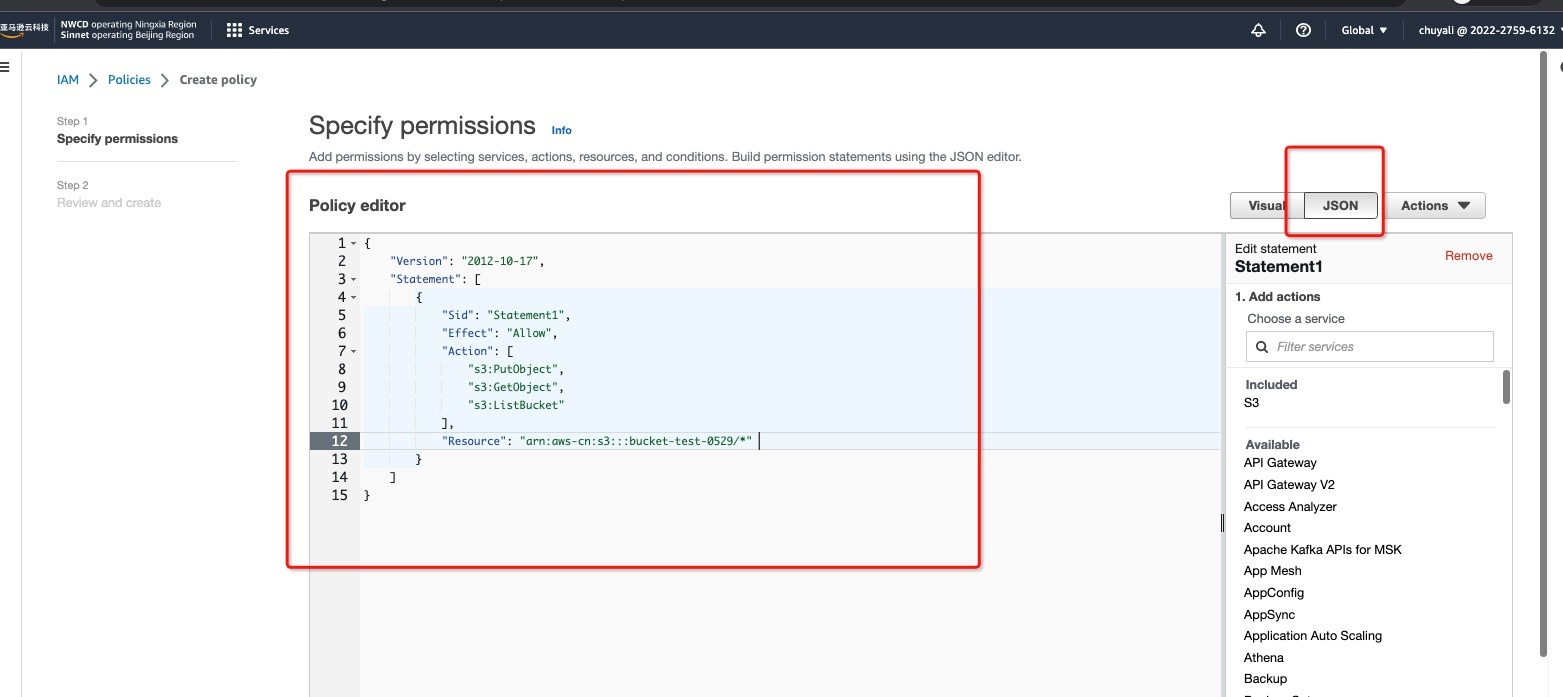
2.3.1 In Create policy > Specify permissions > Policy editor, enter the following content:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws-cn:s3:::<bucket name>",
"arn:aws-cn:s3:::<bucket name>/*"
]
}
]
}
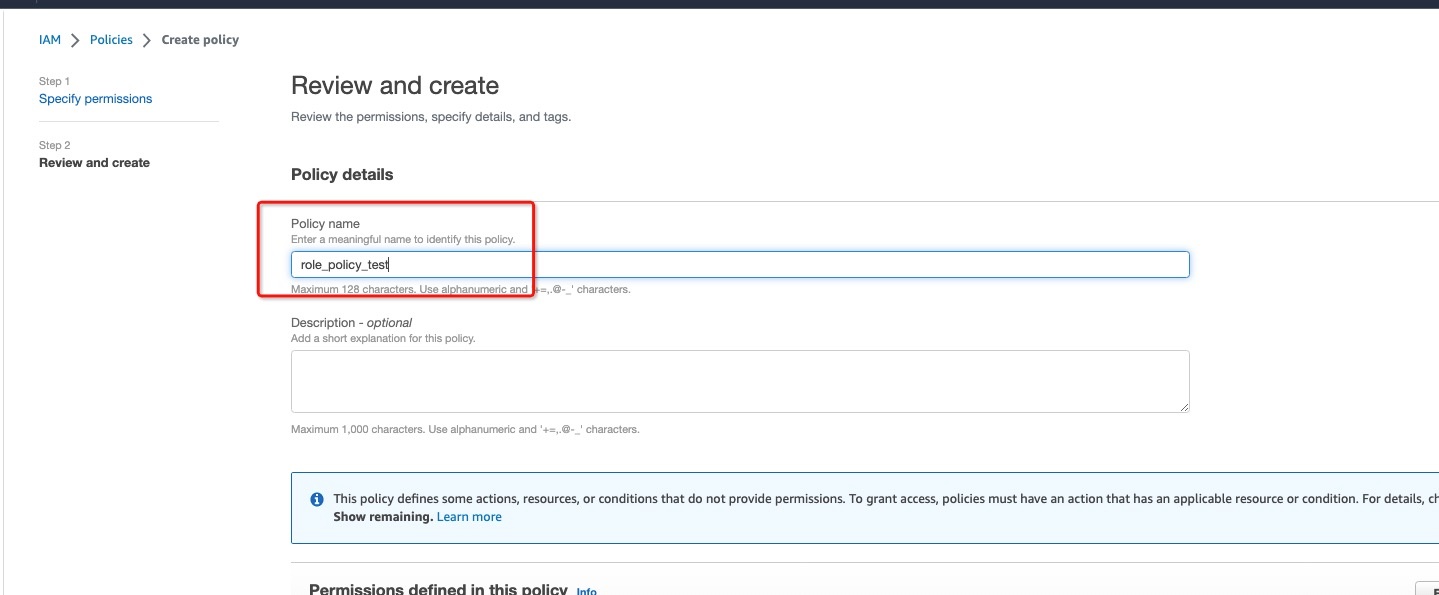
2.3.2 In Review and create > Policy details > Policy name, enter a name to identify this policy, and save the permissions:
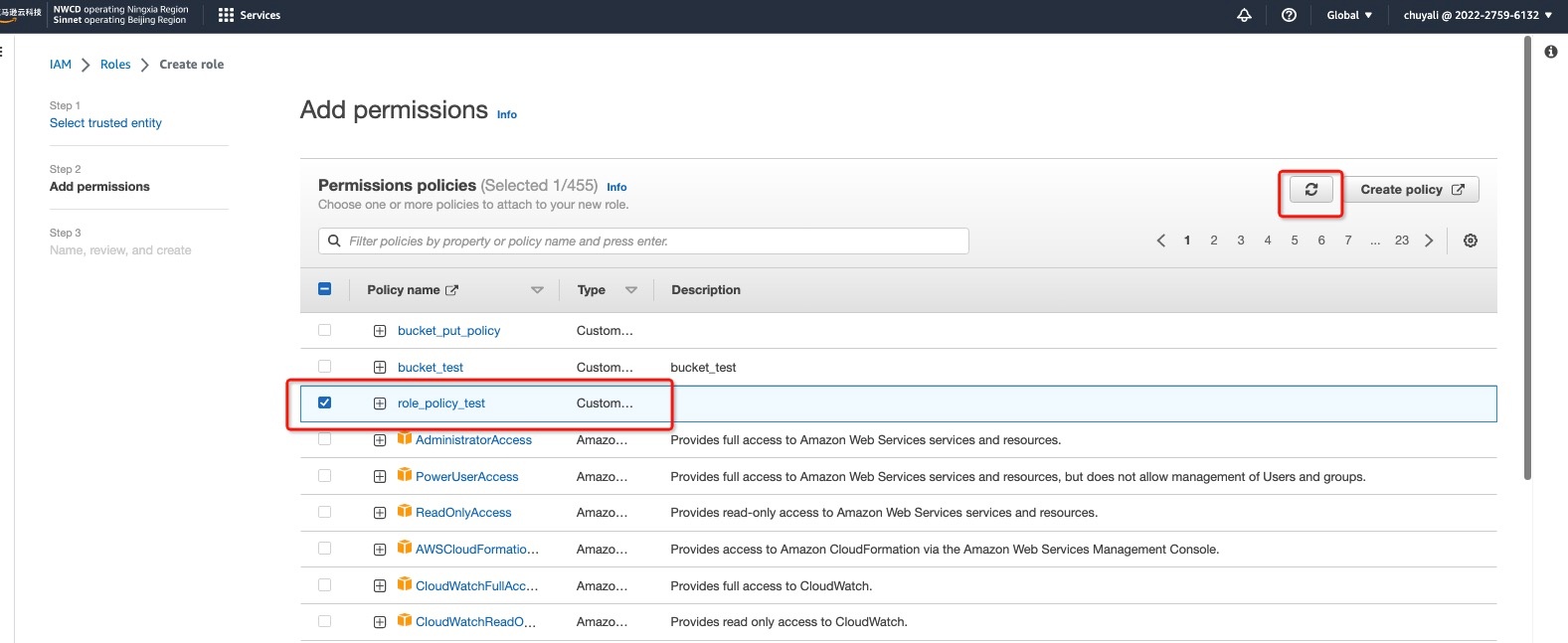
2.4 Return to the Create role interface, click , and the permissions created in the previous step will appear. Select the permissions:
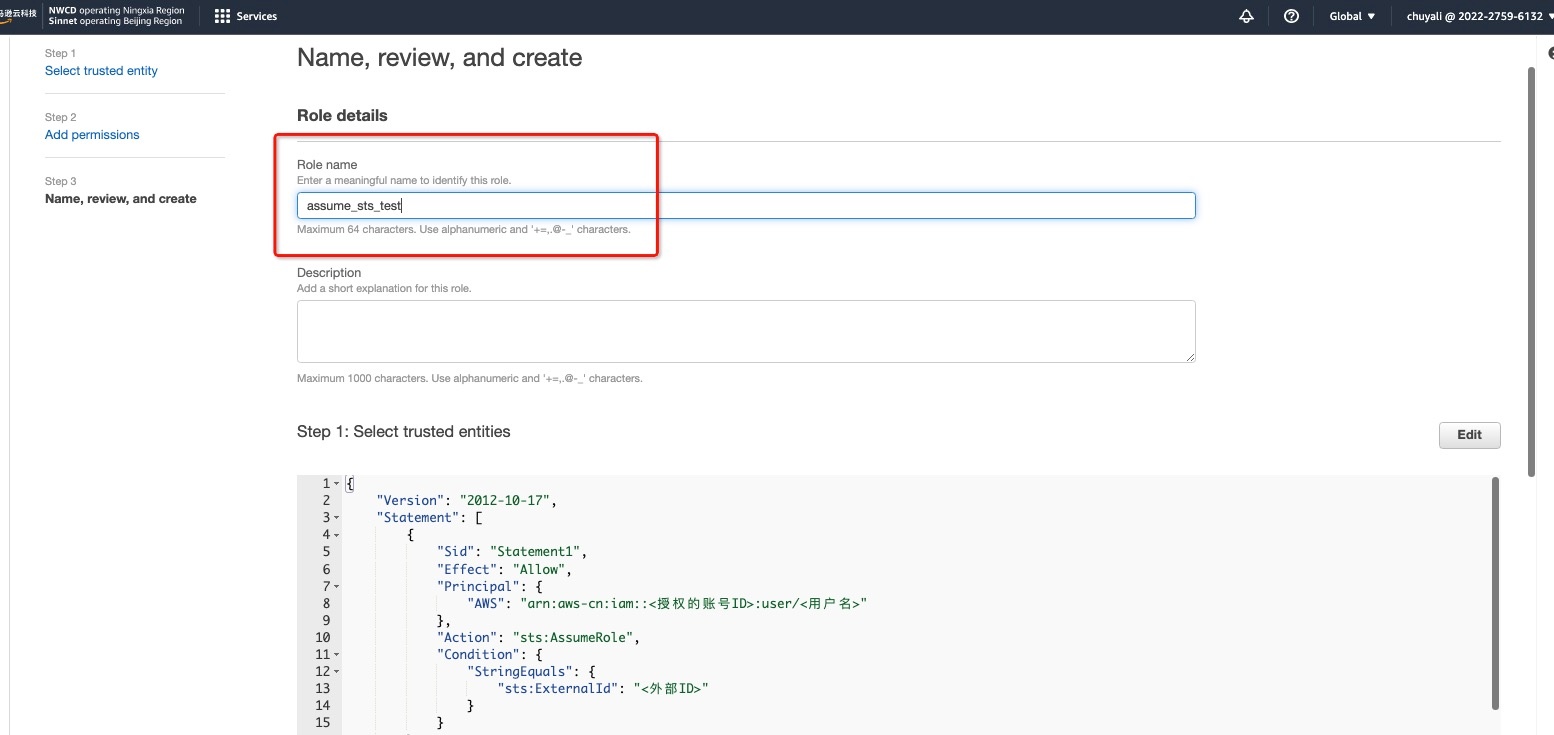
2.5 Enter Step 3 > Name, review, and create > Role detailed name > Role name, fill in the Role name to identify this role, click Create role to complete the authorization. This role name is the AWS Role Name you choose under AWS S3 > Role Authorization > Fill in Archive Information.